- all services
- BMIT Cloud An all-inclusive solution for your growing business - storage, servers and security
- AWS Transform your business with the flexible and scalable AWS cloud solutions.
- Microsoft Azure Get Microsoft Azure for an enterprise-grade cloud computing platform at affordable prices
- MultiCloud Connect Bridge the gap between global cloud platforms.
- Resources & Media
- Blog Hybrid IT - The Future of Business
- all services
- Hybrid Cloud Hybrid Cloud enables the advantages of local hosting with cloud benefits like flexibility and scaling
- Private Cloud Scale your business and dedicated structure with your own Private Cloud
- AWS Transform your business with the flexible and scalable AWS cloud solutions.
- Microsoft Azure Get Microsoft Azure for an enterprise-grade cloud computing platform at affordable prices
- Dedicated Servers Get full control over one of our dedicated servers and cater for your growing business needs
- Managed SysAdmin Ensure smooth running of your IT systems
- Infrastructure Management Efficiently manage your IT infrastructure with our Infrastructure Management service.
- Database Management Reliable data storage services that save you time and costs.
- all services
- Cybersecurity Protect your business with trusted cybersecurity expertise.
- Threat Management Spot vulnerabilities early, test your defences, and building smarter protection so threats are dealt with before they become real problems.
- Virtual CISO (vCISO) Expert security leadership to help you plan, protect, and prepare your business with the right strategy, guidance, and real-world experience.
- Managed Detection and Response Analysts watch over your systems, spotting issues fast, containing threats, and responding quickly so problems are handled before they escalate.
- Cybersecurity Awareness Identify gaps and vulnerabilities in your IT systems and infrastructure with a comprehensive security awareness and assessment service.
- Endpoint & Cloud Protection Protect your Endpoints and Cloud with a raft of advanced security features, services and solutions for devices and Cloud infrastructure
- Network Protection & Management Choose from services such as DDOS mitigation, intrusion prevention & detection, managed firewall, VPN & managed offsite LAN / WAN, to protect your network from attacks.
- Enterprise Data Protection & Recovery Safeguard your data using the latest data encryption, backup, data recovery, data loss protection (DLP), compliance and risk management solutions.
- Identity & Access Management Take control of who has access to your systems or data using the latest Identity & AD management, multi-factor and passwordless authentication, and roles, users, and access policy audit features and technology.
- Email & Web Protection Protects your business from online and email threats such as phishing, malware, and cyberattacks, enhancing your company's cybersecurity posture.
- Vulnerability and Threat Management Effective vulnerability and threat management is crucial for safeguarding sensitive data, maintaining customer trust, and ensuring business continuity.
- all services
- Microsoft 365 A complete, intelligent solution, including Office 365, Windows 10, and Enterprise Mobility + Security
- Migrate to M365 Seamlessly migrate to Microsoft 365 with our reliable migration services
- Hybrid Workplace Advisory Increase productivity and efficiency with our expert Productivity Advisory services
- Managed Backup for M365 Our managed backup solution includes a comprehensive set of tools to backup your M365 data
- all services
- Hosting Compliance Get your hosting compliance requirements up and running, fast.
- DORA BMIT can assist you in reviewing the requirements of DORA. Let’s talk today so you are well prepared from January 2025 onwards.
- IT Governance BMIT’s IT Governance services are tailored to help organisations effectively align their IT strategy with their business objectives.
- all services
- Managed Backup The perfect choice for businesses looking to reduce the effort and upfront costs of setting up, hosting, and managing their backup infrastructure and policy
- Managed Backup for M365 Our managed backup solution includes a comprehensive set of tools to backup your M365 data
- Backup-as-a-Service Securely backup your data with our reliable BMIT Cloud Backup service
- Server & Storage Solutions Boost your workflow for less with our self-service servers, available on-demand
- all services
- Connectivity Services We've partnered with leading international carriers to establish an exclusive private international network
- Managed Network BMIT’s managed network offering provides comprehensive and reliable network services for your business, ensuring seamless connectivity, security, and performance.
- Managed SD-Wan Combine your Wide Area Network (WAN) infrastructure with the agility of Software-Defined Networking (SDN)
- Intersite Connectivity Connect multiple sites or access third-party services through a private network
- MultiCloud Connect Deploy your setup to your preferred global cloud platform, for optimal performance and security
- Wired & Wireless LAN Solutions Ensure a reliable and secure connection, providing coverage and connection throughout the whole business
- Load Balancing Solutions Handle and distribute your traffic effectively with our Load Balancing solution
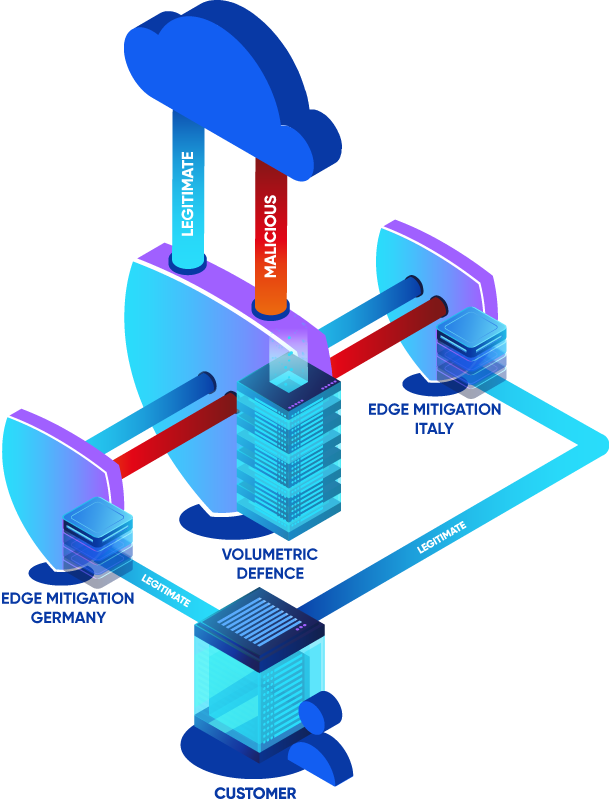
- Managed DDoS Shield BMIT Managed DDoS Shield brings together strong managed capabilities, technology and tools to provide protection tailored to your business’ unique requirements.
- Managed Firewall Whether you go for a traditional or next-generation firewall, BMIT provides the expertise and resources that you may not have in-house or cannot afford.
- Resources & Media
- Blog DDoS Attacks – Are You Prepared?
- Resources & Media
- Web View the partners we work with